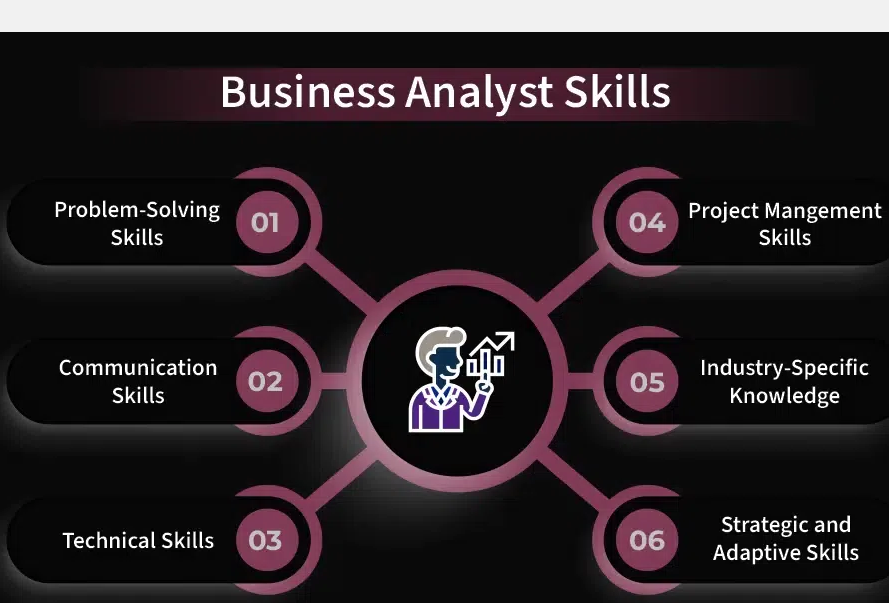
Can Fudo Enterprise Help Prevent Unintentional Privileged User Abuse?

In today’s complex IT environments, managing privileged access is more crucial than ever. Privileged users hold the keys to the kingdom, with access to sensitive systems and data that are vital to an organization’s operation and security. However, this access can also lead to unintentional misuse or abuse, potentially resulting in significant security vulnerabilities. Unintentional privileged user abuse often occurs due to oversight, human error, or lack of awareness about security protocols. Fudo Enterprise offers a comprehensive solution designed to minimize these risks through robust access management, monitoring, and control capabilities. This article explores how Fudo Enterprise can help prevent unintentional privileged user abuse, enhancing overall security and compliance.
Understanding Unintentional Privileged User Abuse
Unintentional abuse of privileged access can involve various scenarios, such as the improper configuration of systems, the accidental sharing of sensitive information, or the unintended installation of unauthorized software. Such actions, although not malicious in intent, can compromise security just as severely as deliberate attacks. The challenge lies in ensuring privileged users can perform their roles efficiently without inadvertently putting the organization’s systems at risk.
Key Features of Fudo Enterprise to Prevent Unintentional Abuse
Fudo Enterprise addresses the issue of unintentional privileged user abuse through multiple targeted features:
- Least Privilege Access Control: Fudo Enterprise implements strict least privilege policies, ensuring that users have access only to the resources necessary for their specific roles. This minimizes the chances of accidental changes or data exposure.
- Just-In-Time Access: Fudo’s Just-In-Time (JIT) access capabilities grant privileges on an as-needed basis, significantly reducing the window during which users can unintentionally misuse their access. Access rights are granted just before they are needed and automatically revoked once the task is completed, limiting the time frame for potential errors.
- Real-Time Monitoring and Alerts: Fudo Enterprise monitors privileged sessions in real-time, providing immediate alerts to system administrators if suspicious or anomalous activities are detected. This feature allows for quick intervention before any unintentional actions result in serious consequences.
- Session Recording and Playback: All user sessions are recorded, creating an audit trail that can be reviewed by administrators. This not only deters unintentional misuse by increasing accountability but also helps identify the root cause of incidents to prevent future occurrences.
- Comprehensive User Activity Logs: Fudo Enterprise logs all user activities, providing detailed context about what actions were taken, by whom, and when. These logs are crucial for uncovering the sequence of events leading to any security incidents, helping to distinguish between intentional misconduct and accidental misuse.
Benefits of Using Fudo Enterprise to Mitigate Unintentional Abuse
Utilizing Fudo Enterprise to manage privileged access comes with several benefits that directly contribute to the prevention of unintentional abuse:
- Enhanced Security: By implementing strict access controls and real-time monitoring, Fudo helps secure critical systems against both intentional and unintentional threats, thereby enhancing the overall security posture of the organization.
- Improved Compliance: Many regulatory standards require that access to sensitive information be carefully controlled and monitored. Fudo’s capabilities support compliance with these regulations, reducing the risk of penalties due to negligent handling of privileged access management.
- Operational Efficiency: Fudo’s JIT access and automation reduce the administrative burden on IT staff, who no longer need to manually grant and revoke access rights. This not only improves efficiency but also decreases the likelihood of human error leading to security vulnerabilities.
- Forensic and Audit Readiness: The detailed logging and session recording features of Fudo Enterprise provide valuable data that can be used for forensic analysis and audit purposes, ensuring that all actions are traceable and accountable.
Conclusion
Fudo Enterprise offers a robust solution to the problem of unintentional privileged user abuse, combining advanced technology with user-friendly controls to safeguard sensitive systems and data. By leveraging Fudo’s comprehensive suite of features, organizations can ensure that their privileged users operate efficiently without compromising the integrity and security of their IT environments. In doing so, Fudo not only helps prevent unintentional abuse but also strengthens the overall resilience of organizations against a broad spectrum of security threats.

Pallet Wood Sourcing: Ethical and Sustainable Practices

Understanding Cost-Benefit Analysis for Project Feasibility
9 Best Free Stock Analysis Websites in 2025

Accelerating drug discovery through the DEL-ML-CS approach

AI in Marketing Is No Longer a Buzzword — It’s the Strategy

Pallet Wood Sourcing: Ethical and Sustainable Practices

Understanding Cost-Benefit Analysis for Project Feasibility
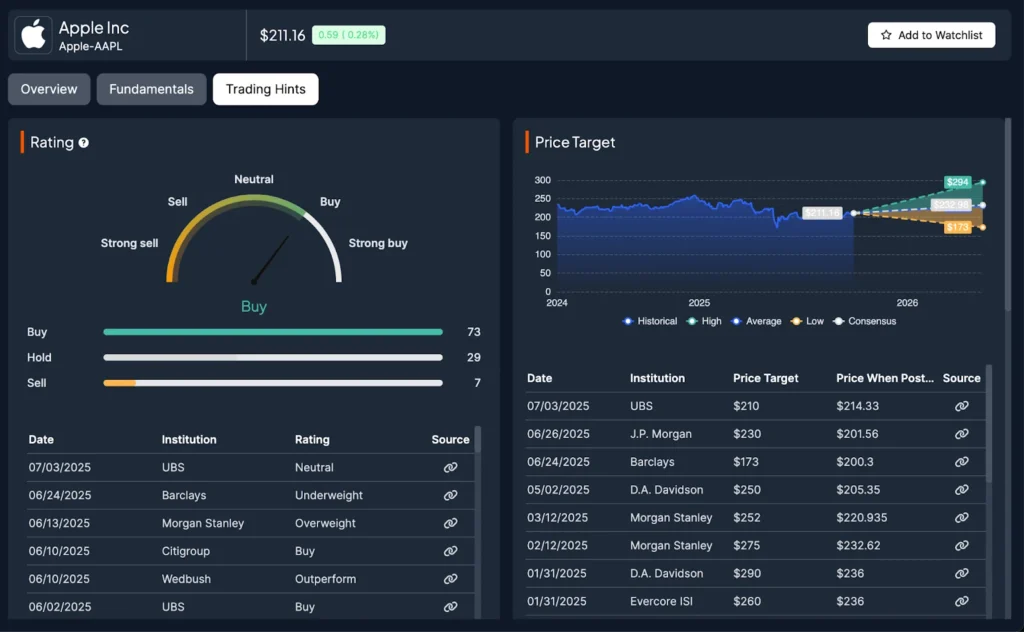
9 Best Free Stock Analysis Websites in 2025