The growing reliance on digital infrastructure for daily business and government operations makes data centers pivotal assets for organizations everywhere. They support essential communications, commerce, and storage for critical data, making them prime targets for various threats.
This reality means that the physical elements of security are no less critical than the digital. Unauthorized physical access to servers, networking hardware, or power supplies could lead to data breaches, downtime, loss, and compliance violations.
The Critical Role of Physical Security in Data Centers
Sophisticated attackers increasingly seek out physical vulnerabilities because, if exploited, these often yield direct entry to sensitive network nodes or backup power. Companies routinely engage expert data center construction services to counteract such risks and build or retrofit facilities with best-in-class security features.
Comprehensive design starts in the planning phase, with ongoing adaptation as new tools and threats emerge, including external and insider-driven attack vectors. Well-implemented physical security creates a robust first line of defense and enhances every other security layer built on top.
Perimeter Barriers and Secure Site Selection
Choosing a secure and strategic site is foundational to any data center. The environment around a building directly determines its vulnerability to accidental hazards—like flooding, landslides, or earthquakes—and intentional threats such as organized crime, industrial espionage, or vandalism.
Security teams collaborate with geologists, city planners, law enforcement, and insurers to evaluate every risk during site selection. Location-specific threats, regional crime rates, and nearby critical infrastructure are thoroughly analyzed. The goal: select a site that is both defensible and operationally advantageous.
Upon selection, proprietary design elements come into play. High fencing and reinforced gates are only initial deterrents. Sites typically employ multiple lines of barrier defense, including anti-ram posts, bollards, and wildlife exclusion measures.
These elements combine to limit vehicular, pedestrian, and airborne intrusions—a concept known as “defense in depth.” Lighting systems illuminate every access point and vehicle route, deterring would-be intruders and increasing visibility even in adverse weather or nocturnal hours.
In addition, the external landscaping strategy is designed to prevent hiding spots and maintain clear sight lines for security patrols and electronic monitoring. Some facilities maintain a perimeter buffer zone—free of structures or dense foliage—so unauthorized personnel become highly visible when approaching the compound. Combining physical design with active surveillance creates a formidable barrier against internal and external risks, ensuring security starts long before the main doors are reached.
Robust Access Controls and Authentication Protocols
Controlling personnel movement into, out of, and within the facility separates secure data centers from traditional office buildings. Multi-factor authentication is the gold standard, requiring something the individual possesses (key card or badge), something they know (PIN or password), and often something they are (biometric data). This layered approach dramatically reduces the risk of misplaced or cloned credentials resulting in successful unauthorized entry.
Physical access points are segmented by function, with different zones for administration, facilities, technical rooms, and server halls. Mantraps or airlocks help prevent tailgating, a surprisingly common method by which unauthorized persons gain access by following staff. Automated access control systems provide detailed logs and can be programmed to trigger alarms for access attempts outside of standard policy, either time-based, personnel-based, or area-based.
Staff and vendors are only granted entry after thorough vetting, and policies ensure that access is time-limited and rigorously reviewed. Lost or stolen badges are immediately revoked from the system. Modern solutions also allow for geo-fencing—remotely denying or granting access depending on an individual’s location or travel status- critical for global organizations with complex operational needs. These systems ‘ regular audits and penetration tests keep defenses sharp and policy enforcement strong.
Surveillance, Monitoring, and Detection Systems
Constant visual and sensor-based monitoring is a fundamental element of physical security. Effective systems feature a combination of high-definition, PTZ (pan-tilt-zoom) cameras covering public and sensitive spaces, with feeds transmitted to a secure command center staffed 24/7. Artificial intelligence analysis can help identify emerging threats by detecting unusual behavioral patterns, clustering in parking areas, or movement in restricted zones during odd hours.
Integrating motion and vibration sensors with video analytics further strengthens early warning capabilities. Alarms can trigger automated lockdowns, while remote monitoring teams validate alerts before escalation. In regions with unreliable power or connectivity, redundant local storage secures video evidence even if the main building management system is disrupted. Some data centers leverage drones or perimeter robotics to continuously monitor large or multi-building campuses, combining rapid response with cost-effective patrol operations.
Surveillance also forms the basis for continuous improvement. Reviewing incident footage supports thorough investigations and informs policy enhancements. Employees are trained to respond when surveillance alerts are issued, maximizing the value of robust monitoring infrastructure by ensuring it is fully integrated into real-world response plans.
Internal Security Zones and Segmentation Strategies
Internal zoning minimizes lateral threat movement within the building. By limiting who can access what areas inside the data center, organizations restrict the potential impact if a single layer of defense fails. High-risk environments—such as those hosting government data or financial platforms—often mandate five or more distinct secure zones, each with strictly enforced controls and alarms.
Color-coded zones, distinct security check-ins, and biometric readers help enforce boundaries. Data halls are typically the most heavily protected, with environmental sensors monitoring temperature, humidity, and unexpected movement alongside traditional security measures. Reliable segmentation is crucial in multi-tenant facilities—where client separation must be absolute—to preserve trust and regulatory compliance.
These approaches not only thwart inside threats but also facilitate business continuity. Should an incident arise, the containment nature of security zones prevents escalation and supports orderly investigation and remediation without impacting unaffected systems or staff. Integrated systems allow for rapid lockdown of zones and evacuation of personnel during emergencies, while enabling detailed visibility into real-time personnel movement and area occupancy.
Visitor Management and Personnel Procedures
Visitor management aligns directly with transparency and risk management. Every interaction, delivery, contractor visit, or inspection is logged with purpose, duration, and identification. Unescorted access is extremely rare; two-person rules or dual authentication may be mandatory during high-risk operations. Visitor badges are programmed to deactivate after set intervals, and the handover of visitor identification is strictly enforced at exit.
Comprehensive human resource protocols include extensive background checks, ongoing security clearance reviews, and regular employee security training. These programs educate all staff—from executives to delivery personnel—on the threat landscape and the importance of situational awareness. Social engineering awareness modules help mitigate risks from psychologically manipulative attackers who attempt to gain access by exploiting human vulnerabilities, such as impersonation, deception, or misplaced trust.
Internally, established protocols define rules for key management, mobile device policies, and securing confidential material. With whistleblower protections and defined escalation paths, employees are empowered to report suspected policy violations. Frequent drills test emergency preparedness and routine compliance, reinforcing a culture where vigilance is every person’s responsibility.
Resilience Through Redundancy and Emergency Planning
Physical defense is only half the story—robust data center security is measured just as much by the facility’s capacity to continue operations under stress. Infrastructures are built with multiple power grids, automatic failover generators, redundant HVAC and cooling systems, fire detection and suppression equipment, backup water and fuel supplies, and dual network paths. These components guarantee service availability even if one or more individual elements fail.
Detailed emergency response protocols address a range of scenarios. Security teams conduct scenario training for fire, flood, earthquake, civil unrest, pandemics, and targeted attacks. Plans are rehearsed with local authorities and first responders, ensuring a coordinated and prompt response. Drills review emergency communication protocols, the operation of backup systems, and safe shutdown or data migration procedures.
The goal is uninterrupted or quickly restored customer service, no matter the adversity.
Data centers further conduct regular vulnerability assessments on emergency infrastructure—inspecting generators, fire suppression systems, and critical spares inventory. Well-maintained documentation, secure off-site backups, and transparent communication with clients all play roles in a rapid and organized recovery, supporting trust and regulatory compliance.
Compliance, Industry Standards, and Continuous Improvement
Meeting or exceeding global physical security benchmarks is not only a customer expectation but also a legal necessity for many operators. Most leading-edge data centers seek or maintain compliance with frameworks such as ISO 27001 for Information Security Management, SSAE 18 for auditing, and PCI-DSS for payment data environments. These broad standards address physical access and monitoring, incident response, staff training, and continual risk assessment.
Compliance is an evolving process—annual audits, third-party penetration tests, and regular policy updates ensure adaptation to new threats and technologies. Staying engaged with developments from organizations like the International Energy Agency helps teams keep pace with emerging standards and international best practices.
Even if minor, post-incident reviews provide an opportunity to update defenses, reinforce policies, and invest further in staff training. A continuous improvement cycle ensures the facility is always positioned one step ahead of the threat landscape.
Conclusion: Building Trust Through Physical Security Leadership
Investing in robust physical security measures is more than a compliance checkbox—it’s a strategic commitment to data integrity, uptime, and brand reputation. In an era when the cost of a breach can include financial loss, regulatory penalties, and irreparable trust erosion, data center leaders must view physical resilience as a core business priority.
By adopting a layered, proactive approach—from site selection and barriers to real-time monitoring, zoning, robust emergency planning, and adherence to global standards—organizations build confidence among their clients and partners.
Ongoing learning, regular reviews, and a willingness to adopt new technologies—from smart surveillance and biometric access to advanced response drills and risk modeling—further cement the data center’s status as a trusted foundation for modern digital life. Updates from sources such as data center news and global research agencies keep decision-makers alert to evolving threats and solutions.
As the digital landscape grows in complexity, organizations that champion physical security leadership will help define the benchmarks of tomorrow’s resilient, trustworthy, and highly available digital infrastructure.

Why Retail Software Testing is Critical for Effective E-commerce Development?

How Sales Teams Increased Productivity with Parallel Dialers

Curtain Dry Cleaning and Leather Sofa Cleaning – Reliable Care by Duo Nini

LLM-Native Software Architecture: Designing Products for Agents, Not Just Humans

Bespoke in the South: How Charlotte’s Elite Are Personalizing Their Rolls-Royce
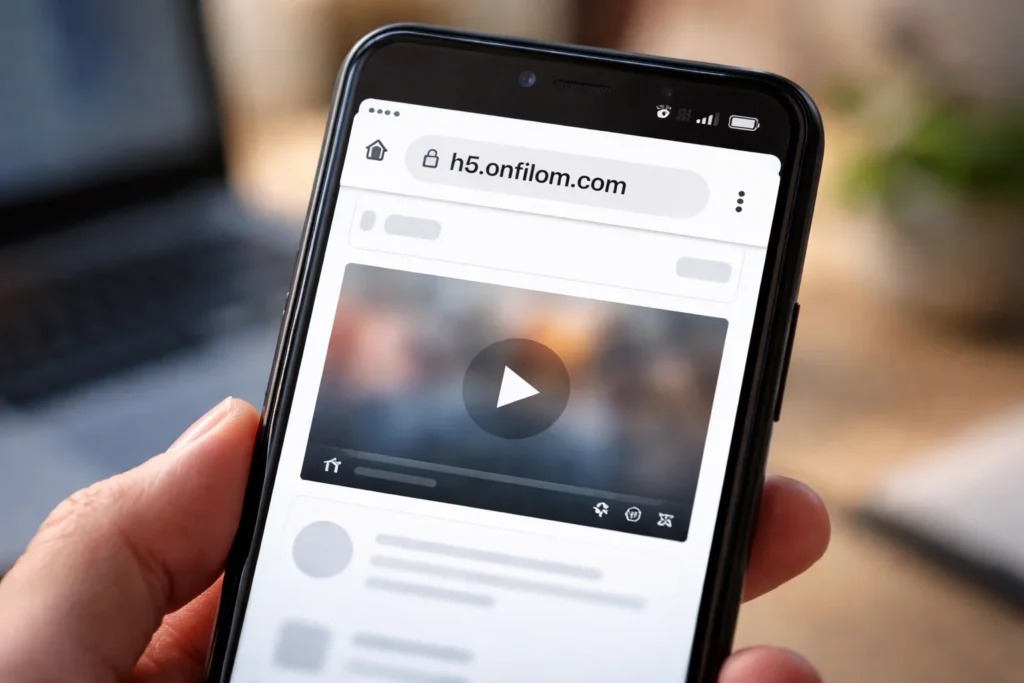
h5.onfilom.com: What It Is, Why It Appears, and How Users Should Treat It
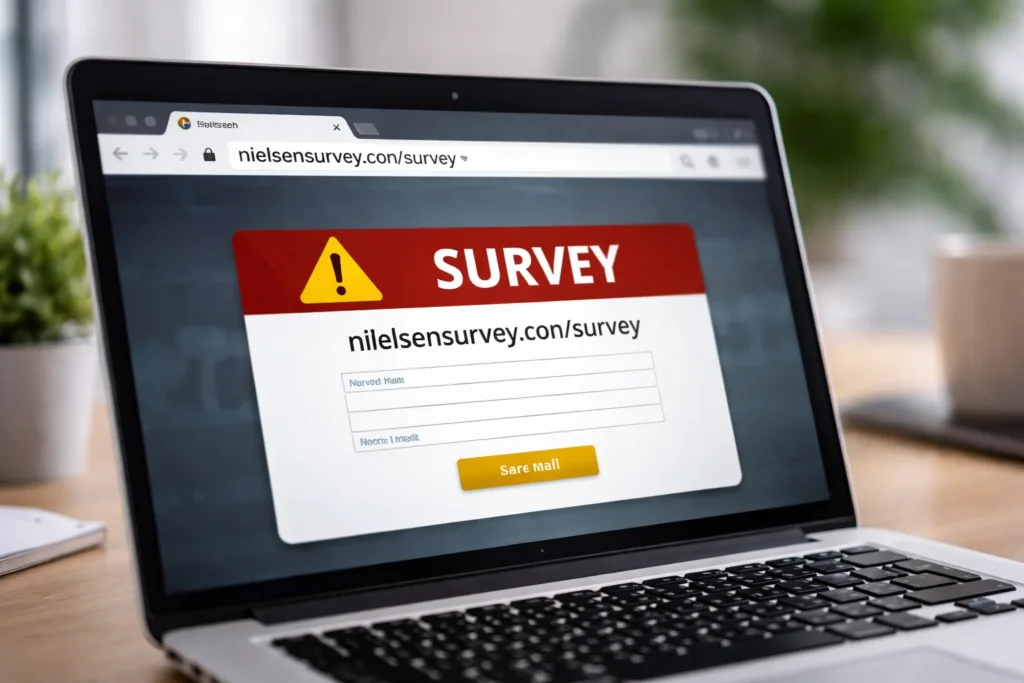
nielsensurvey.con/survey – Real Nielsen Survey or Fake Link? Complete Safety Guide

Strong Password Guide: Create & Manage Safe Logins